Apache2 is not used on our servers for many reasons including low productivity and high resource consuming. That is why instead of usual work with .htaccess files you can configure nginx.
You need to know
- You are inside the block, writing the rules
server { ... } - Only two directives are allowed: location and if
- All illegal directives are cut out saving configurations, without an error report
- After saving the configuration, it is tested by nginx and if there are any mistakes – previous working configuration is opened.
- Php-process that serves your site is called backend-login, for example – backend-s55
- Standard redirect on index.php for MODX is called @rewrite
- If you save an empty window, a standard configuration will be added
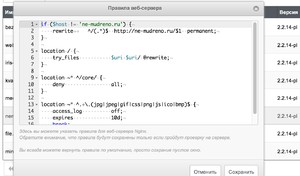 If you are not familiar with it, check the parameters lower
If you are not familiar with it, check the parameters lower
Useful examples
Redirect from all the domains, including service, to one canonical host
if ($host != 'mysite.ru') {
return 301 http://mysite.ru$request_uri;
}*It is suitable for redirect organization with www. And without-www.**
Redirect from one definite domain
if ($host = 'mysite.ru') {
return 301 http://not-my-site.ru$request_uri;
}Redirect from index.php to a web-site root
if ($request_uri ~* '^/index.php$') {
return 301 /;
}Addition of slashes to addresses in the end
if ($request_uri !~* "(?:\?)|(?:\.\w+$)|(?:\/$)") {
return 301 $request_uri/;
}Remove slash at the end of the address
If you have changed the address of the MODX manager, then you need to specify it in the condition of this rule, otherwise it will be an endless redirect.
if ($request_uri ~ ".*/$") {
rewrite ^/((?!manager|setup).*)/$ /$1 permanent;
}Remove .html extension
You need to edit already existing block for the location /:
location / {
try_files $uri $uri/ @rewrite;
rewrite ^/(.*?).html$ /$1 permanent;
}Redirect to protocol https
if ($scheme = 'http') {
return 301 https://$host$request_uri;
}Prohibition of access to MODX service directory from all ip addresses, apart from definite:
If a limited number of manager use website admin from the same ip addresses, it is reasonable to limit the access to service directories only for them:
location ~* ^/(manager|core|connectors)/ {
allow 196.198.15.183;
allow 135.158.250.19;
deny all;
# If a used passed the test, he will not exit this block
# That is why a definite work with php is required here
location ~* \.php$ {
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_pass backend-s55; # Pay attention to the name of php process
}
}Basic authorization to service directories
More universal prohibition to service directories for undefined number of people with dynamic ip is basic authorization.
It is a password request from a web-server that works until php files and it protects you from possible vulnerabilities in authorization work of “slider”.
You have to generate .htpasswd file on this service and upload it to your directory, upper /www.
A file is a simple list of user names with hashtagged passwords with delimiter. On default, one user is added but you can generate several files more this way and just copy the lines from them to the first one. Every user is on one individual line! Passwords in this file should not concur with the password in admin; otherwise, there is no point in such defense.
Now you have to indicate Nginx and use your file .htpasswd to access service directories.
location ~* ^/(manager|core|connectors)/ {
auth_basic "Restricted Access";
auth_basic_user_file /home/yourlogin/.htpasswd;
try_files $uri $uri/ @rewrite;
location ~ \.php$ {
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_pass backend-yourlogin;
}
}Entering your admin, you will see basic authorization:
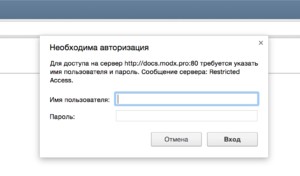
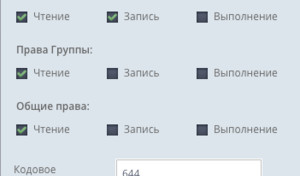
Attention! If you are creating a file through the file manager Sprut - be sure to check its attributes.
File permissions must be equal to 644, otherwise Nginx will not be able to read it and you will receive a 500 error when authorizing.
Rule conversion
If you already have ready rules for Apache2, you can try to convert them to Nginx rules with online converter.
